Today I tackle Forest, an Easy Windows box. This one's all about LDAP, my achilles heel. In the end, it actually took me 2 days... :S
The name "Forest" references an LDAP forest, and that should have been my warning. But since I'm in this to tackle these weak spots, maybe it's better I DIDN'T catch the hint. I also took some time over the 2 days to get myself set up for an upcoming 72-hour hacking challenge/technical interview.
Out-of-the-gate, I started off well, and got the user flag in reasonably short order. But we were just dipping our toes in to LDAP at that point. This is where Bloodhound came in to play. I found it while seraching for some privilege escalation options here. From my quick work with the tool, it "scans" the entire Active Directory, and can help find "connections" between entities. So it can find a series of groups-within-groups and privileges and settings that can allow a user to somehow gain access to, for example, and Domain Administrator. It can also do a whole lot more, way more than I was able to even really wrap my head around on this single box. But using this information, I was able to find a path to Admin by abusing the AD group memberships and security settings.
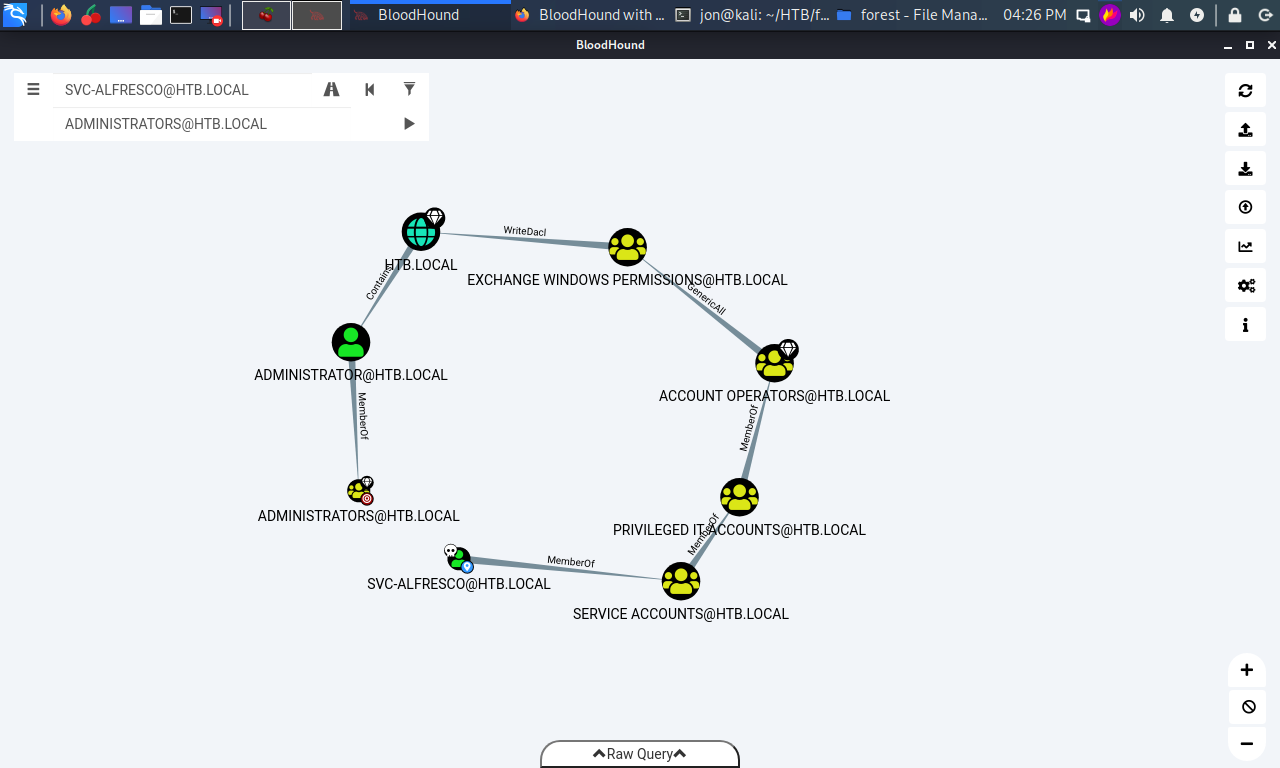
And here's where things got really hairy for me... A got the user flag, I figured out the next step beoing that I had to abuse a WriteDACL permission. I even figured out what commands on my Kali box to run, aclpwn. Except that it didn't work, I got all kinds of python errors. So I searched and searched and tried things and serached and tried some more, but nothing I did would make the command actually work. So back to more searching, and I find a different option to escalate, Invoke-ACLPwn.ps1, to be run on the "victim" box. There's a few other binaries required, and after getting that all set up, I run it. And get errors. So search and try and search and try some more, no matter what I try, nothing can get the script to work either. So back to the searching (and at this point reaching out to friends on Discord and Slack), and I eventually stumble across this. While I didn't get any errors per se, it never seemed to complete and I never got anything else to move forward.
At this point, I started to despair. Like, really, seriously despair. Maybe I'm not cut out for these things after all...
Fortunately, real-life interrupted my despair and I didn't get to wallow in my misery for too long. Until I went to sleep that is... but that's a whole different story...lol...
Next day (today), I had a few more things to address, then got back to the box. Looking over the previous day's work, I make a few more feeble attempts, but it was clear I wasn't going to succeed down these routes. Since I had been using this Kali setup for a while, and installing gods-knows what, it wouldn't surprise me if I broke something (everything) along the way. So I spin up a new Kali install, and get thw whole set of errors and problems all over again.
My searches weren't turning up anything new either. There's was some really obscure/technical stuff, but this is supposed to be an EASY box, not something so convoluted and obscure. My despair grew. In a moment of weakness, I caved and looked up an existing writeup for the box.
To my horror, it was solved with the aclpwn command. No mention of any errors. No mentions of any problems. Just ran the command and was then able to get password hashes.
Well... Maybe it's just this author... Maybe they just skipped over the problems and errors they encountered. So I checked another.
The next was solved with the Invoke-ACLPwn.ps1 script. Again, no mention of any problem nor errors. Just ran the script, got hashes. On to the next.
Another aclpwn. Another Invoke-ACLPwn script.
Eventually I found one using the 3rd option I found, ntlmrelayx.py. There too, no problems. Ran the commands, got hashes.
NO ONE is having ANY errors nor problems. Some of the writeups DID go in to such details as they encountered them. But NO ONE was having the problems *I* was having, and *I* couldn't figure out how to get these otherwise simple commands to work. I was beyond despair. I was haing a full on imposter syndrome attack. I began to seriously doubt whether or not I have any business applyting to any kind of Ethical Hacker positions, let alone get invited to a hacking challenge for one.
HTB has an Official Discord channel, and though I reached out a couple times there before, I did so again, much more pleadingly. In my discussions with the admin who responded, I was reassured that I was indeed going down the right path. The commands I was providing were in fact the very commands that SHOULD work. Barring the Kali errors, the ntlmrelayx command should be working. In the end, it turned out there was some kind of "cleanup script" taking place behind-the-scenes, approximately every 10 minutes. So there was a bit of pre-work that needed to be in place for the ntlmrelayx to work, and once I got it in place, I had, AT MOST, 10 minutes to accomplish the next few steps. BUT, depending on precisely when the script last ran and when my work was done, it is entirely possible that, SECONDS (maybe) after accomplishing my ground work, the script "erased" it before I could get the next step.
SO WHERE I WAS GETTING THE RIGHT THINGS DONE, I HAD UNKNOWN FORCES SABOTAGING ME BEHIND MY BACK!!!
As soon as it was made clear to me that my ground work was being unknowingly destroyed, BOOM! I got the rest sorted out in no time, and get the root flag within 5 minutes of this information. It was a very strange combination of... rage, that I was being sabotaged like that, and... relief, that maybe, just MAYBE, I have a bit of an idea of what I am doing.
Report for Forest on HTB |
|
 Thursday, 13 August 2020 18:35 Thursday, 13 August 2020 18:35  467.13 KB 467.13 KB  567 567 |
Download |
In this box, we didn't actually leverage any "exploits" per se. We simply abused LDAP features and functions, and Group memberships and security settings. It really highlights the needs to treat your AD servers like "The Crown Jewels", and ensure they are not accessible by any potential threat actors.
Beyond that, to be quite honest, is beyond my current LDAP knowledge. Given this isn't anything overly out-of-the-box, I would suspect there's probably some existing readings on the matter, along with the remediations. If this were a “real world” engagement, I would absolutely be reading up some more on those, but also take a bit more time (days maybe) reading up an coming up with something clever. But given this is day 2 on what was supposed to be a single-box-a-day challenge, I wil leave it at that.

