A quick google search for "crack wifi" will return tons and tons of results. Take a quick peek at any of the results, and they will literally walk you through, command by command, and crack a WiFi passphrase within 6 steps. Within 5 minutes, you can read several of these walkthroughs. It looks so easy! Could it really be that simple? Truth be told, it isn't...
For the sake of discussion, let us first walk through cracking a WiFi passphrase (the fun stuff!).
Preparations!
"BE PREPARED" - Scouts Motto
To start, we will need some WiFi cracking tools, specifically:
- airmon-ng
- airodump-ng
- aireplay-ng
- aircrack-ng
NOTE: These are all part of the Aircrack-ng suite.
How to get them? There are 3 primary options:
Lastly, we need a WiFi card compatible with Aircrack-ng. They have a great document detailing their compatability here.
Get Cracking!
So, once you've get things ready to go, let's crack some passphrases.
- Put Wi-Fi Adapter in Monitor Mode with Airmon-Ng
airmon-ng start wlan0
- Display raw WiFi network info with Airodump-ng
airodump-ng mon0- Here you will see the raw details for the available networks, find your target here
- Start capturing packets for the target network:
airodump-ng --bssid 08:86:30:74:22:76 -c 6 --write WPAcrack mon0- '-c' is the channel, found in the output from Step 2
- In another terminal window, start sending deauth packets to force some WPA handshakes
aireplay-ng --deauth 100 -a 08:86:30:74:22:76 mon0
- Have an eye on the output from Step 3. We need to capture a WPA handshake, and in the top line to the far right, airodump-ng will show "WPA handshake: " when one has been captured. Once you have it, Ctrl+c to stop the capture.
- Let's Aircrack-ng that passphrase!
aircrack-ng WPAcrack*.cap -w /path/to/wordlist
- When aircrack-ng show "KEY FOUND", your key is within the square bracket [ ], and you are DONE!
Caveats
But is it really so easy? Yes, and no... Allow me to explain:
Yes - Yes, it really is that simple to crack a WiFi WPA2 passphrase. Go through these 6 steps, and you can crack that passphrase. I can personally attest to this; I followed the process above, and cracked a test WiFi passphrase.
No - There are some rather key details missing here. Let me elaborate:
- First off, Step 3. Here, we need to capture a WPA handshake. This happens when the WiFi "client" connects to the access point; thus Step 4, sending the deauth packets to force a new handshake. So this means that if you are testing this yourself, in the sterility of a lab-type environment, you will need a WiFi "client" to connect to your access point. If there are no clients using the WiFi, you will never get that handshake.
- Also, if the WiFi is distributed to multiple Access Points (as is the case with many corporate environments), your deauth packets might work, but due to the distributed nature of the WiFi network, the clients are likely to connect to a different access point than the one you are watching. So you may need to be patient while you simply wait for a handshake to take place.
- Step 6. Here, we need a wordlist. There are many MANY worlists out there, ranging from raw dictionary words to complex hacking specific lists. CrackStation has a pretty big list here, and SkullSecurity has a nice list here. But there is 1 simple fact that is not really ever mentioned anywhere: if the passphrase is NOT in the list, you will NOT crack it.
To demonstrate this, I took a page from an XKCD Comic:

Going with this comic, I tested this very thing. First, I set a WiFi passphrase: Tr0ub4dor&3 .
Using the above methods, and a combination of different wordlists, I was able to crack the passphrase in a few hours (most of the time was waiting on the cracking itself).
I then went and made the passphrase: correcthorsebatterystaple .
Using the same methods, and an even greater number of wordlists, I have yet to crack this passphrase, even using dictionary wordlists. Nearly 1 BILLION passphrases attempted, and no luck:
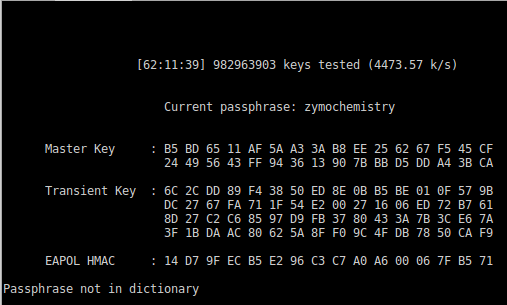
I then went and created my own wordlist (a plain text file, 1 entry per line), and only put in correcthorsebatterystaple, and using this wordlist, the passphrase was cracked almost instantly. Even though 'correct', 'horse', 'battery', and 'staple' are all in the dictionary worlists individually, there is no single entry of 'correcthorsebatterystaple', so it would never be cracked with those lists.
In the end, the "hidden strength" of these tools isn't really the tools themselves (though they are just as equally powerful), but in the wordlist(s) that you use to try to crack the WiFi. This fact is rarely specifically mentioned, and is thus the "Unspoken" truth about WiFi cracking.
Go ahead and let me know what you think in the comments section below.
Reference:
http://lewiscomputerhowto.blogspot.ca/2014/06/how-to-hack-wpawpa2-wi-fi-with-kali.html
